What is LBL Cybersecurity's policy on using VPNs?
- LBL IT recommends you use VPN when conducting LBL-related work off of the lab campus. If you use VPN, we require using the Lab's official VPN, Cisco VPN, which can be downloaded here.
- Our Acceptable Use Policy allows for incidental personal use, even on the LBL VPN, as long as it doesn't violate other Acceptable Use Policy requirements. For example, if you're traveling or using untrusted wireless networks but need to check your personal email, that is perfectly acceptable.
- Using any commercial or free VPNs on LBL-owned devices is not allowed. We may specifically block the usage of certain commercial or free VPNs as required by DOE. Even if a block is not in place for a specific commercial or free VPN, we still recommend use of the Lab’s official VPN.
- We recommend caution when using any commercial or free VPN on personally-owned devices or for personal use. Details about why are below.
Acceptable external VPN usage
It's acceptable and can be required to use the VPN service of another research facility, university, or vendor to access their resources. This may require using the AnyConnect client with a different profile or even a another VPN client such as Global Connect.
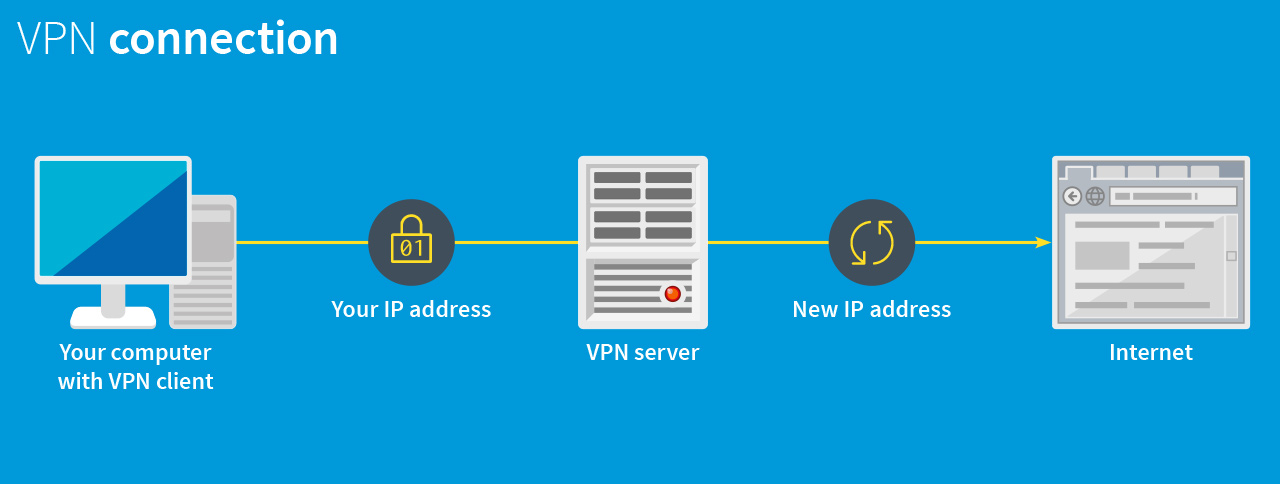
What is a VPN?
A Virtual Private Network (VPN) is a technology that enables your computer to appear on another network. It does this by creating an encrypted tunnel between your computer and another computer (or hardware appliance) on another network, called a VPN server, and encapsulating your network traffic inside of that tunnel. The VPN server on the other end de-encrypts and de-encapsulates your traffic, and sends it off to its final destination. The return traffic is then sent to the VPN server rather than directly to your computer, and the VPN server similarly encapsulates and encrypts that traffic and sends it to you.
Source: GData
How does the Lab's official VPN differ from a Commercial or Free VPN?
The Lab's official VPN is operated by the Lab's networking group, LBLnet. The LBL VPN servers are located in LBL data centers, on the LBL network, and using it makes your computer appear as if it is physically on the LBL campus. That means it will inherit all the usual cybersecurity and privacy protections available to any computer at the Lab. However, it also means that your network traffic is subject to monitoring, both by the Lab's Cybersecurity group and by DOE, so you should ensure that your usage while connected to the Lab's VPN follows our Acceptable Use Policy.
In contrast, a Commercial or Free VPN is operated by a private company, and they are unbeholden to the Lab's, the University of California's, or the Department of Energy's privacy or cybersecurity policies. While connected to a Commercial or Free VPN, your network traffic is sent over an encrypted tunnel to an outside network, preventing the Lab's cybersecurity team from having any visibility into potentially malicious traffic, or applying many of our normal cybersecurity controls to protect against compromises.
What are our concerns related to using a Commercial or Free VPN?
- Commercial or Free VPN provider’s incentives may not align with LBL’s
As a private company, a Commercial or Free VPN provider has different legal requirements and financial motivations than LBL. Depending on where they are operated, they may not be required to safeguard your personal information from reselling to third parties, or they may even be required to turn over your personal information to non-US governments. - Commercial or Free VPNs may be less secure
The Commercial or Free VPN provider may not take appropriate steps to protect your device or your personal information from attackers. Recall that a VPN essentially puts your computer on another network. If an attacker is using the same network and the VPN provider hasn't put appropriate controls in place, you may be more vulnerable to attack than when your computer is either on your home network, or on the Lab's network. - Using a Commercial or Free VPNs may cause LBL to block your network traffic
Attackers have used Commercial and Free VPNs to attack the Lab in the past, causing us to block IP addresses that you may be trying to use as a customer of the service. As there generally isn't a 1:1 relationship of customers to IP addresses, your legitimate activity may even be intermingled with attack traffic from a different customer. - Using a Commercial or Free VPN makes it more difficult for LBL cyber to protect you
If you're on the Lab's network and using a Commercial or Free VPN, all of your network traffic is encapsulated inside of the encrypted tunnel, preventing the Lab's cybersecurity group from detecting or preventing malicious traffic. For example, if your computer becomes infected with malware while using a Commercial or Free VPN, we won't be able to detect the infection or command & control traffic used by attackers. - Commercial and Free VPN providers can monitor your traffic
Commercial and Free VPNs often market themselves as a more secure and private alternative to using untrusted networks, such as a coffee shop or hotel. However, due to a VPN essentially putting your computer on another network and sending all of your traffic through it, the VPN provider has the ability to see your traffic just as much as a coffee shop or hotel operator would. Should you trust the VPN provider more than the coffee shop or hotel owner? Even a well intentioned VPN provider will have a larger target on their back for attackers than the average coffee shop or hotel, simply due to the nature of their customers. - Your traffic may appear malicious to LBL Cyber
Some Commercial or Free VPN providers implement a reciprocal, peer-to-peer technology, meaning your traffic isn't just sent through a VPN server they operate, but is sent through other customers' computers, and in turn, other customers' traffic is sent through your computer. This can cause a large number of issues, from malicious traffic appearing to originate from your computer to allowing unaffiliated individuals access to LBL networks. Sometimes these services don't even claim to be a VPN, but rather a "traffic anonymizer".