|
|
||||||||||||||||||
| Pop away |
|---|
| Warning | ||
|---|---|---|
| ||
The current Simulated Phishing campaign has ended, and signups are no longer being accepted. Examples of past Simulated Phishing campaigns are still provided below for reference. |
In order to raise awareness of current phishing scam attack tactics, the Berkeley Lab Cyber Security team will begin sending sends emails to the Berkeley Lab employees that simulate real phishing attacks. During the initial phases of this project simulated phishing emails will only be sent to list of users who opt-in to receive them. Information about individual responses will NOT be shared with supervisors or HR.
If you would like to help improve Berkeley Lab's phishing awareness please sign up below.
The goal of this simulated phishing campaign is to help you to learn how to spot a phish and report them to it to the Cyber Security team. Accurately reporting phishing allows the Cyber Security team to alert other employees and block future attacksphishes.
Opting in
What to do when I see a phishing email
What is phishing?
Spam, Phishing, Targetted Phishing
Phishing
If you receive a phishing email, please report it to [email protected] and use our spam reporting procedures to send the spam to our anti-spam vendors.
Phishing is an attack that attempts to acquire sensitive information, such as usernames or passwords. Phishing attempts frequently attempt to trick you into visiting an invalid website. For example, many phishing attempts redirect you to sites that appear to be eBay, Citibank, or PayPal, but are actually not. The phishers are trying to trick you into typing your username, password and other sensitive information into these invalid website's. The phishers would then steal your username and password to use on the real eBay, Citibank, or PayPal.
Targeted Phishing
If you receive a phishing email, please immediately report it to [email protected]
Cyber criminals are using sophisticated targeted phishing attacks to compromise computers at Berkeley Lab. The attack emails refer to familiar scientific projects, conferences, or experiments and may appear to come from colleagues, your supervisor, or even lab management. The attackers craft the messages to trick you into clicking a malicious attachment or link. Did you know a single click can compromise your system? Unfortunately, you cannot count on antivirus software to protect you from these attacks since the malware is designed to avoid detection. This is a hard problem.
The best defense for these attacks is to be aware of the attack methodology, remain vigilant, and report anything suspicious. If you receive an email that looks suspicious, asks for information or action, and is specifically targeted at you in the context of your affiliation with Berkeley Lab, UCB, UC, or DOE, please forward it as an attachment to [email protected]. Computer Protection Program is interested in anything that falls within the category of "targeted social engineering".
See the social engineering page for more information.
----
Phishing is a type of attack carried out in order to steal usernames, passwords, credit card information, Social Security Numbers, and other sensitive data by masquerading as a trustworthy entity. Phishing is most often seen on campus in the form of malicious emails pretending to be from credible sources such as UC Berkeley technology departments or financial organizations related to the university.
By tricking campus users into giving away their information, attackers can:
- Steal money from victims (modify direct deposit information, drain bank accounts)
- Perform identity theft (run up charges on credit cards, open new accounts)
- Send spam from compromised email accounts
- Use your credentials to access other campus systems, attack other systems, steal confidential University data, and jeopardize the mission of the campus
The goal of most Phishing emails is to trick you into visiting a web site in order to steal your CalNet credentials. Attackers will setup web sites under their control that look and feel like legitimate web sites. Often the Phishing emails will have an immediate call to action that demand you to "update your account information" or "login to confirm ownership of your account". If you enter your CalNet credentials into these illegitimate web sites you are actually sending your CalNet username and password directly to the attackers.
Why is this necessary?
How will it be implemented?
How can you avoid phishing scams?
Training and Resources
Examples:
Sign up
Simulated phishing emails will be sent only to users that have filled out this Sign Up Form.
What is Phishing?
An important part of this campaign is distinguishing between what is a phishing email, a targeted phishing email, and spam.
| Attack | Description | Action you should take | ||||||||
| Targeted Phishing | A phishing attack that targets your affiliation with Berkeley Lab, UCB, or DOE to steal | Report immediately to [email protected] | ||||||||
| Phishing | Attacks that are carried out in order to steal passwords, SSNs, and other sensitive data. These messages often ask you to click on a link, send information, or enter credentials by pretending to be a credible website (such as a bank). | Report to [email protected] | ||||||||
| Spam | These are unwanted messages but are not asking for sensitive information. | Good to update spam filters by using our
|
How do I report a phishing email?
Send an email to [email protected] reporting the incident and include the source code of the phishing email as an attachment. If you do not know how to attach the source code click here to learn how to forward the source code of an email as an attachment:
| Link in New Window | ||||||
|---|---|---|---|---|---|---|
|
FAQ
I think I received a simulated phish, what should I do with it?
Please report simulated phishing just as you real phishing, by either using the Chrome Phishme Reporter extension or by forwarding to [email protected]
Privacy
Information about individual responses will NOT be shared with anyone outside the security team. Passwords will NOT be stored. This information will never be used or released in any identifiable manner outside the security group, including in any manner which would be used to evaluate your job performance. Simulated phishing is designed as a training exercise and to help the Laboratory understand our overall exposure to phishing as well as to target our protections and training. It is in no way designed and will not be used to judge the performance of individuals.
Feedback
In order to improve this program please fill out this form after receiving a simulated phishing email
Past Simulated Phishing Campaigns
Below are screenshots of the simulated phishing campaigns that have been run so far at LBNL.
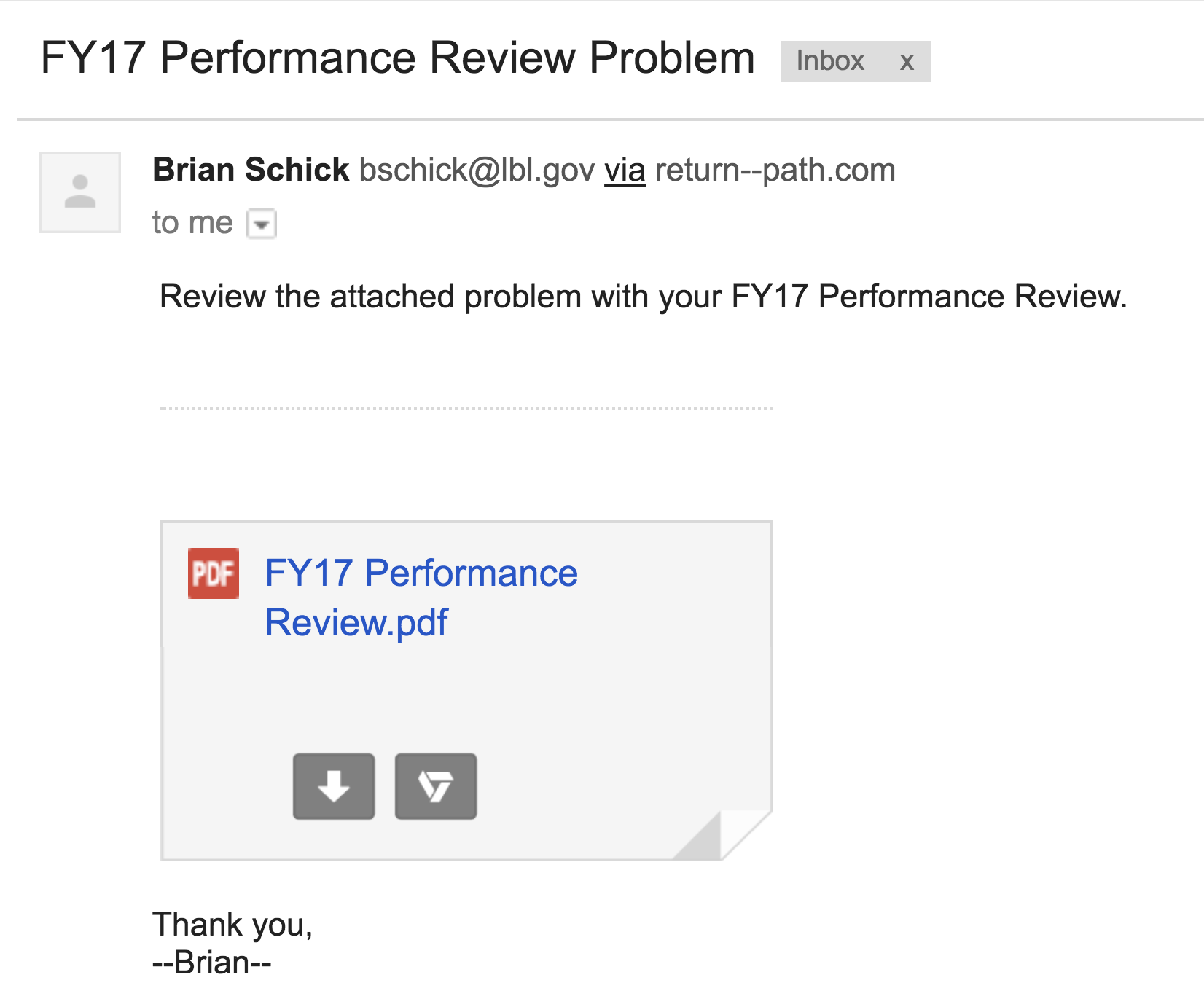
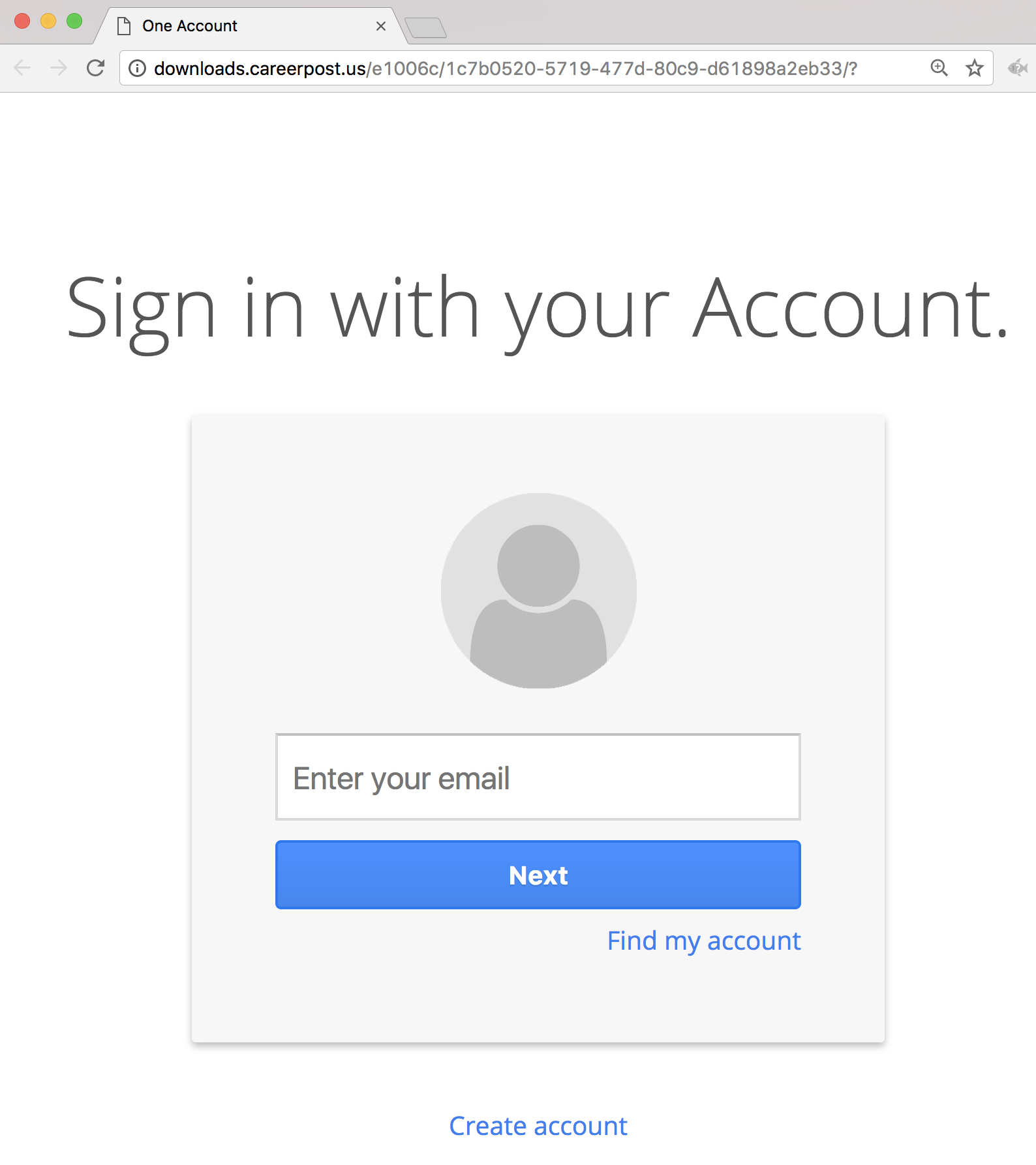
#5 2017-10-16: FY17 Performance Review Problem
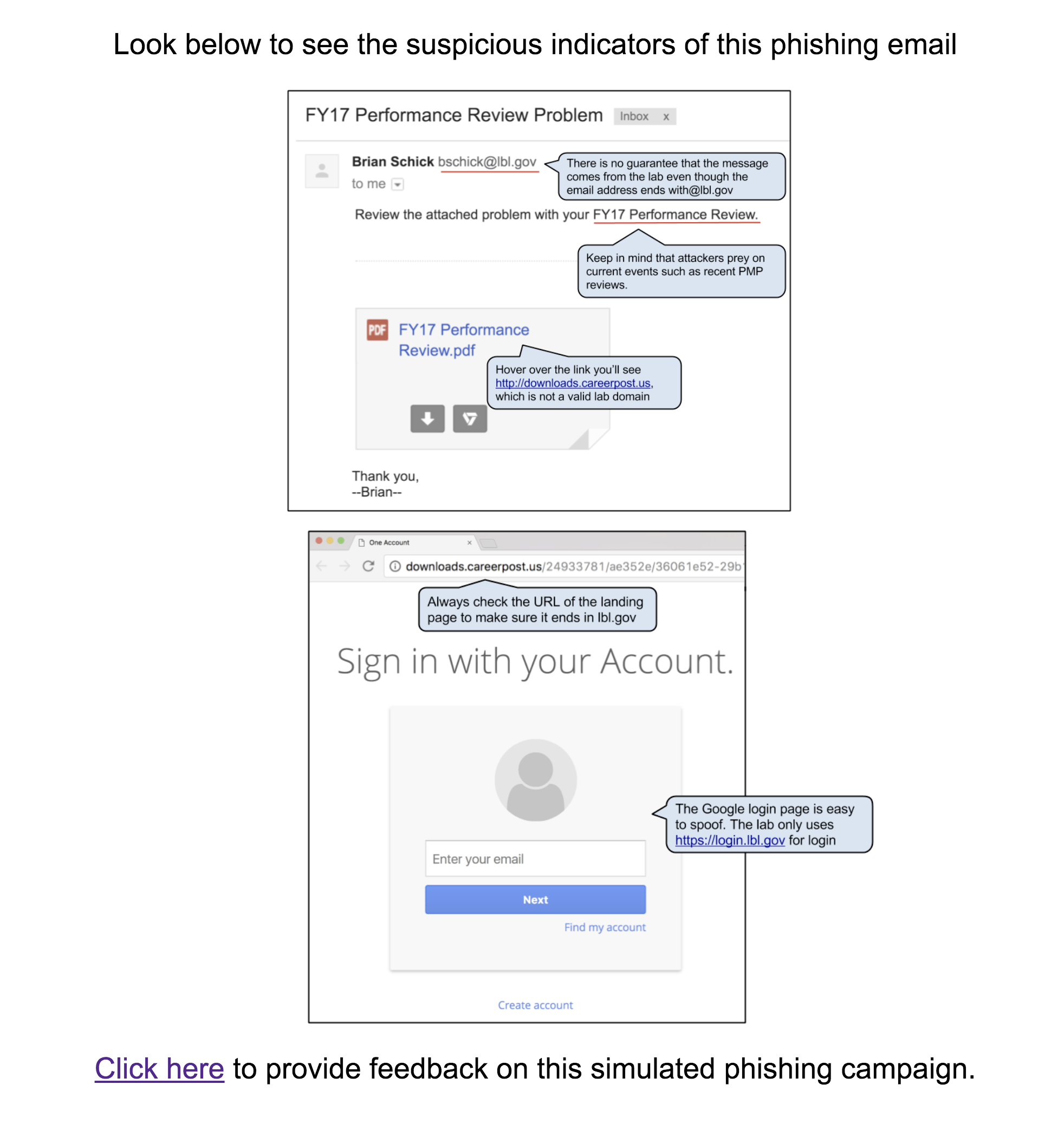
This email was intended to get users to question the legitimacy of the pdf attachment even though the sender appears to have a “real” lbl.gov email address. The attachment link in the email directed to a spoofed google login page in order to retrieve the username and password of the user. The fake employee Brian Schick was created to demonstrate the situation where an email address is spoofed or compromised. Emails sent to Brian was answered by the security group.
Users were expected check for Brian Schick on the directory as well as notice they were being asked to log in with LBL credentials to a non-LBL site.
Sender: Brian Schick - [email protected]
Link: http://downloads.careerpost.us/
The Email:
The Landing Page:
The Education Page:
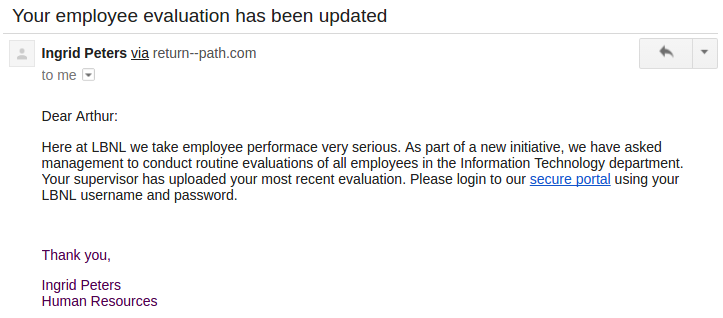
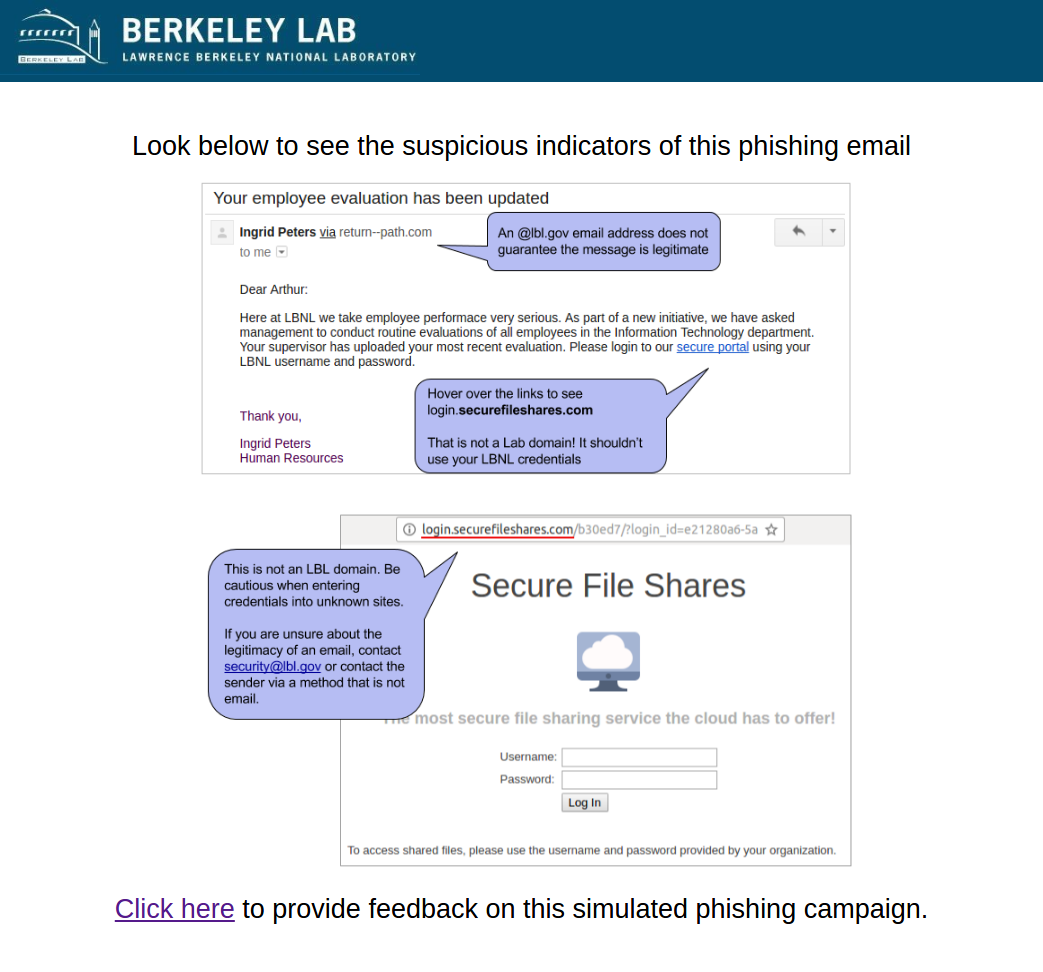
#4 2017-03-14: Employee evaluation
This email was intended to get users to question the request to input credentials into a non-LBL site. The link in the email directed to a non-LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was reused from the previous phish. Ingrid was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security group.
Users were expected to notice that they were being asked to log in with LBL credentials to a non-LBL site as well as notice the reuse of the [email protected] address.
Sender: Ingrid Peters - [email protected]
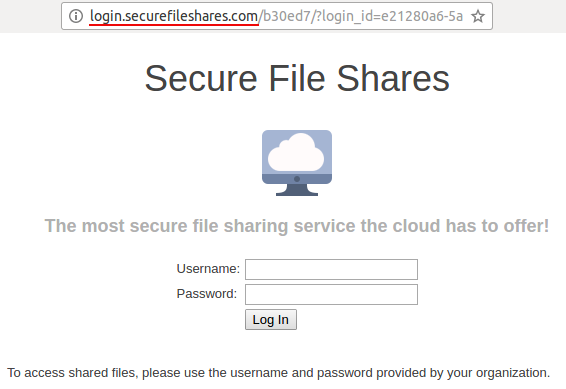
Link: http://login.securefileshares.com
The Email:
The Landing Page:
The Education Page:
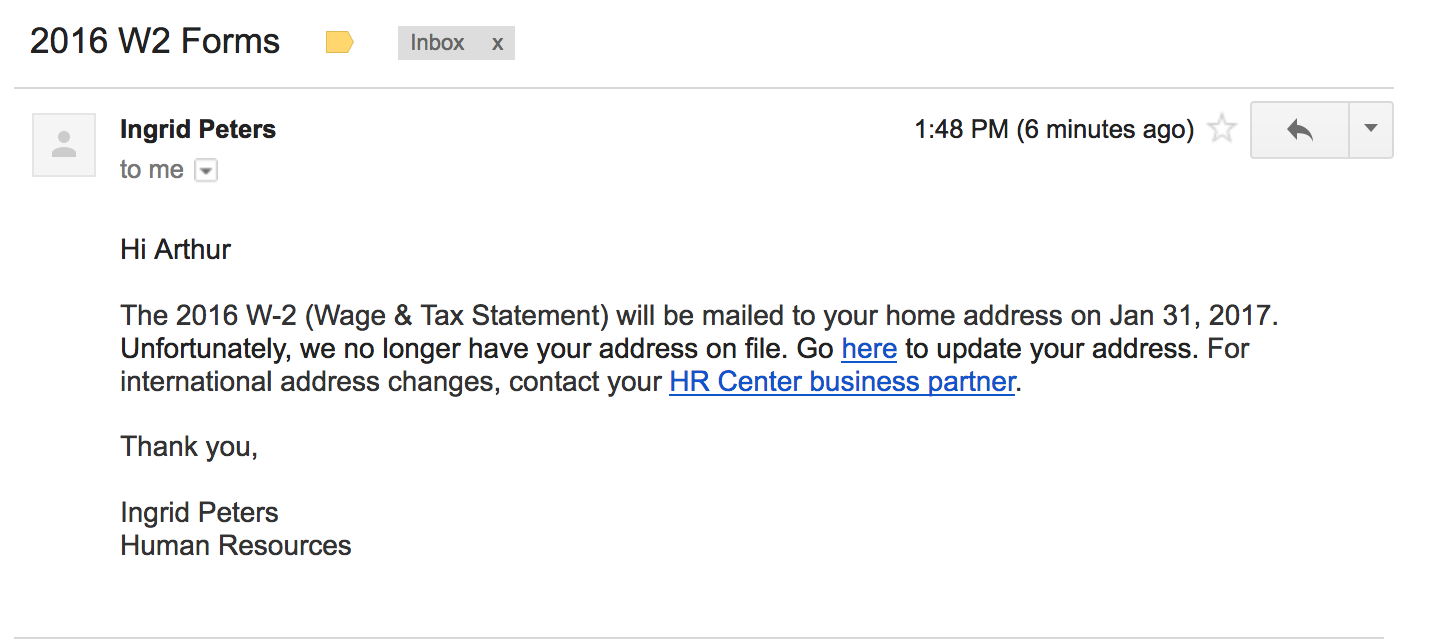
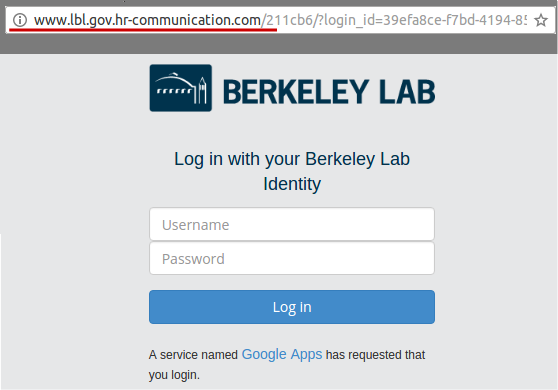
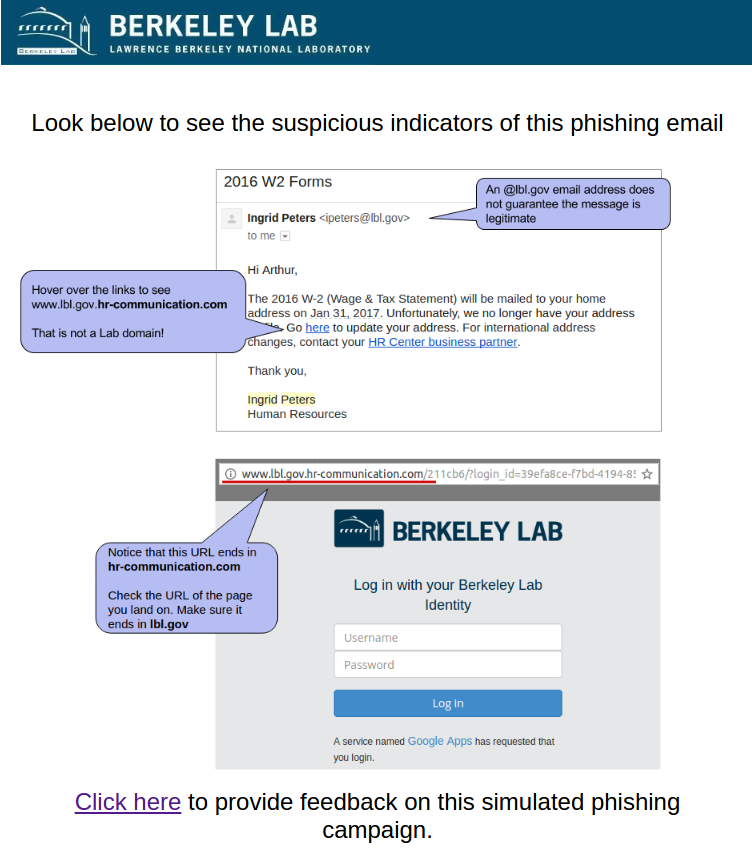
#3 2017-01-18: 2016 W2 Forms - lost mailing address
This email was intended to get users to focus on the URL despite the use of a "real" lbl.gov email address. The link in the email directed to a fake LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security group.
Users were expected to notice the non-LBL link that the email directed to or to call the number for Ingrid Peters to check the validity of the email out-of-band.
Sender: Ingrid Peters - [email protected]
Link: http://www.lbl.gov.hr-communication.com/
The Email:
The Landing Page:
The Education Page:
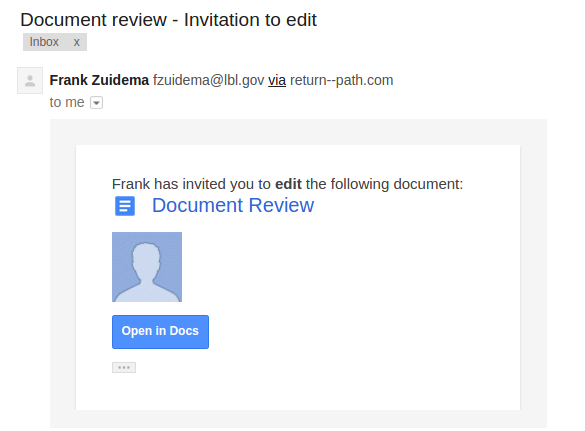
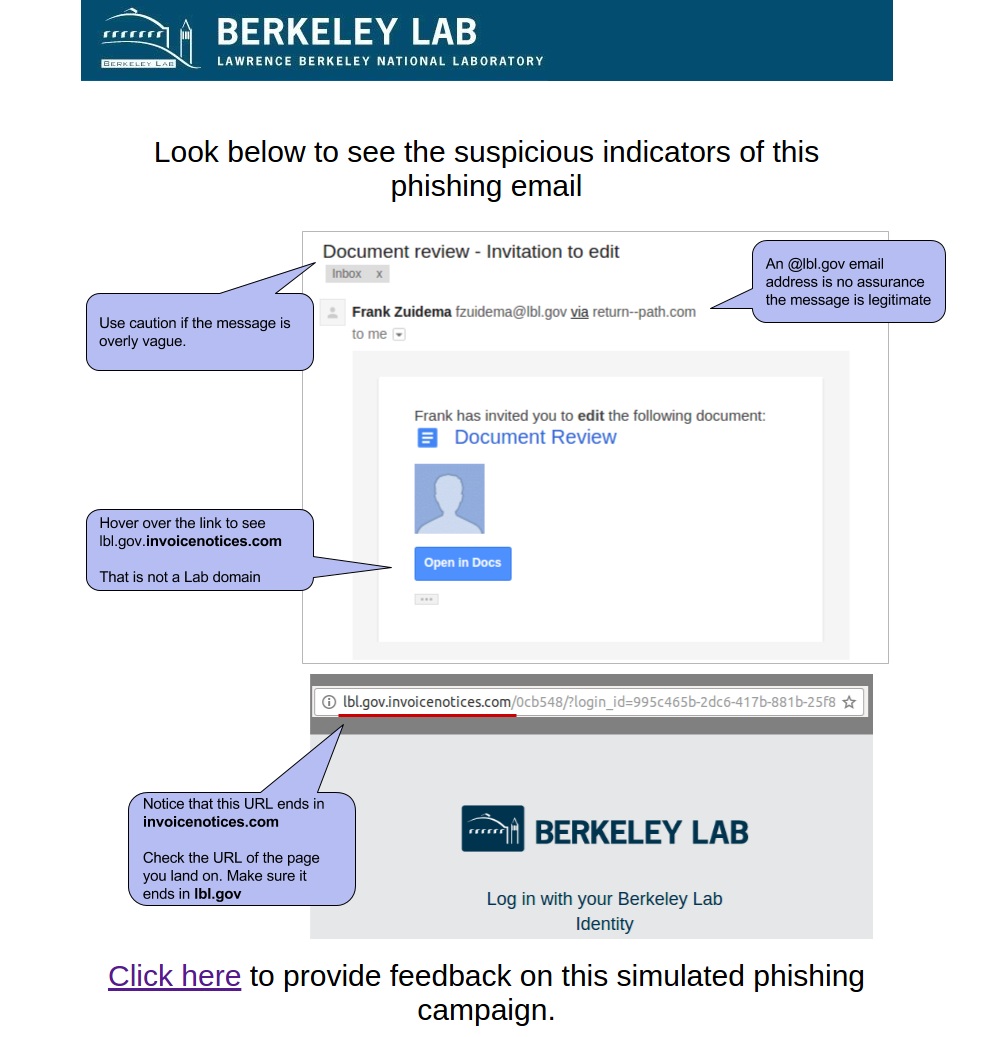
#2 2016-12-06: Google Document Invitation to edit
This email was intended to get users to focus on the URL and demonstrate that it is often trivial to make a email or web site that looks like ones you trust. It mimicked the HTML of a real "Invitation to Edit" email sent by Google Drive as well as the LBL login page. The email appeared to be from an LBL employee (although this user doesn't exist).
Users were expected to notice the non-LBL link that the email directed to or check the existence of the sender.
Sender: [email protected] - Frank Zuidema
Link: http://lbl.gov.invoicenotices.com
The Email:
The Landing Page:
The Education Page:
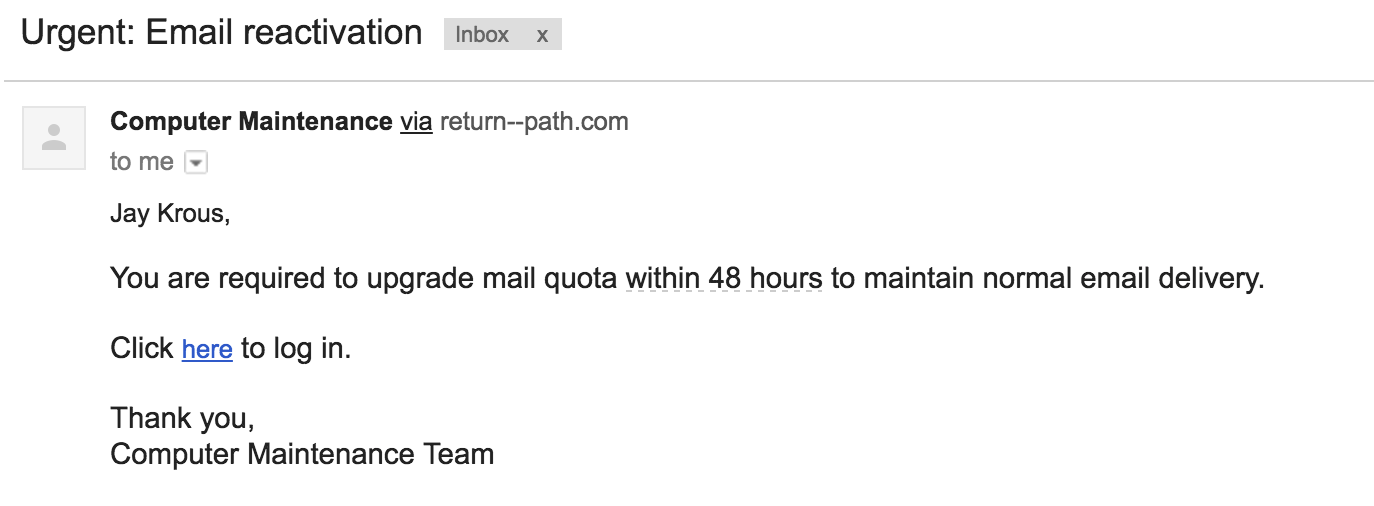
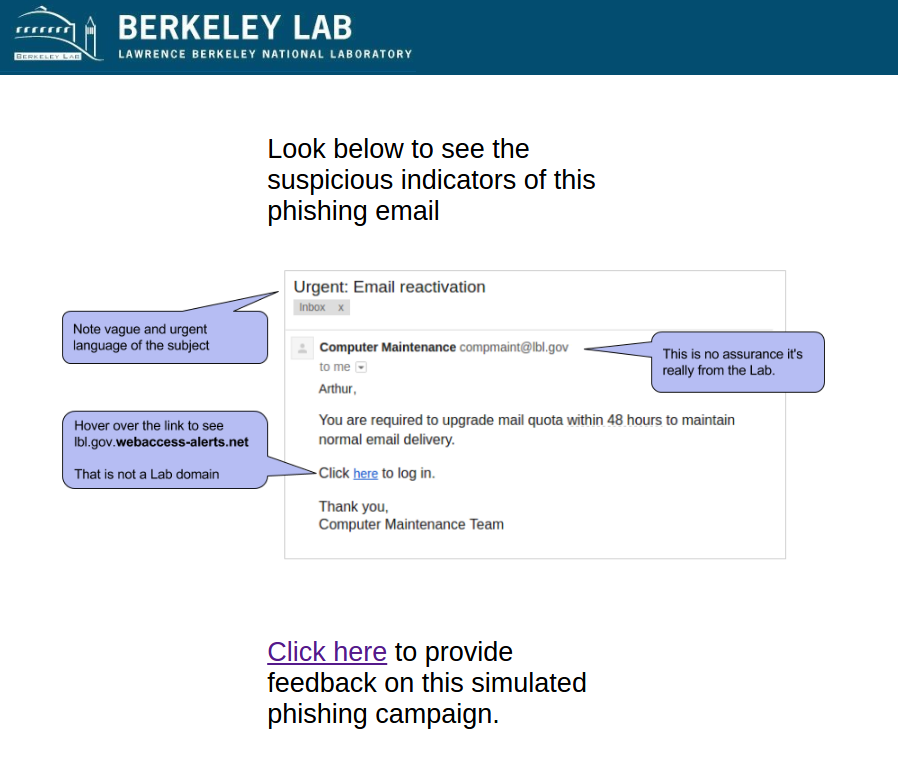
#1 2016-10-08: Urgent - Email Reactivation
This email was our first phish and intended to test the waters. It emulated the common phishing emails that are vague, urgent, and not necessarily relevant. It had an fake sender address that appeared to be from within LBNL.
Sender: [email protected] - Computer Maintenance
Link: http://lbl.gov.webaccess-alerts.net/
The Email:
The Education Page:
Opt-in