|
|
||||||||||||||||||
...
Below are screenshots of the simulated phishing campaigns that have been run so far at LBNL.
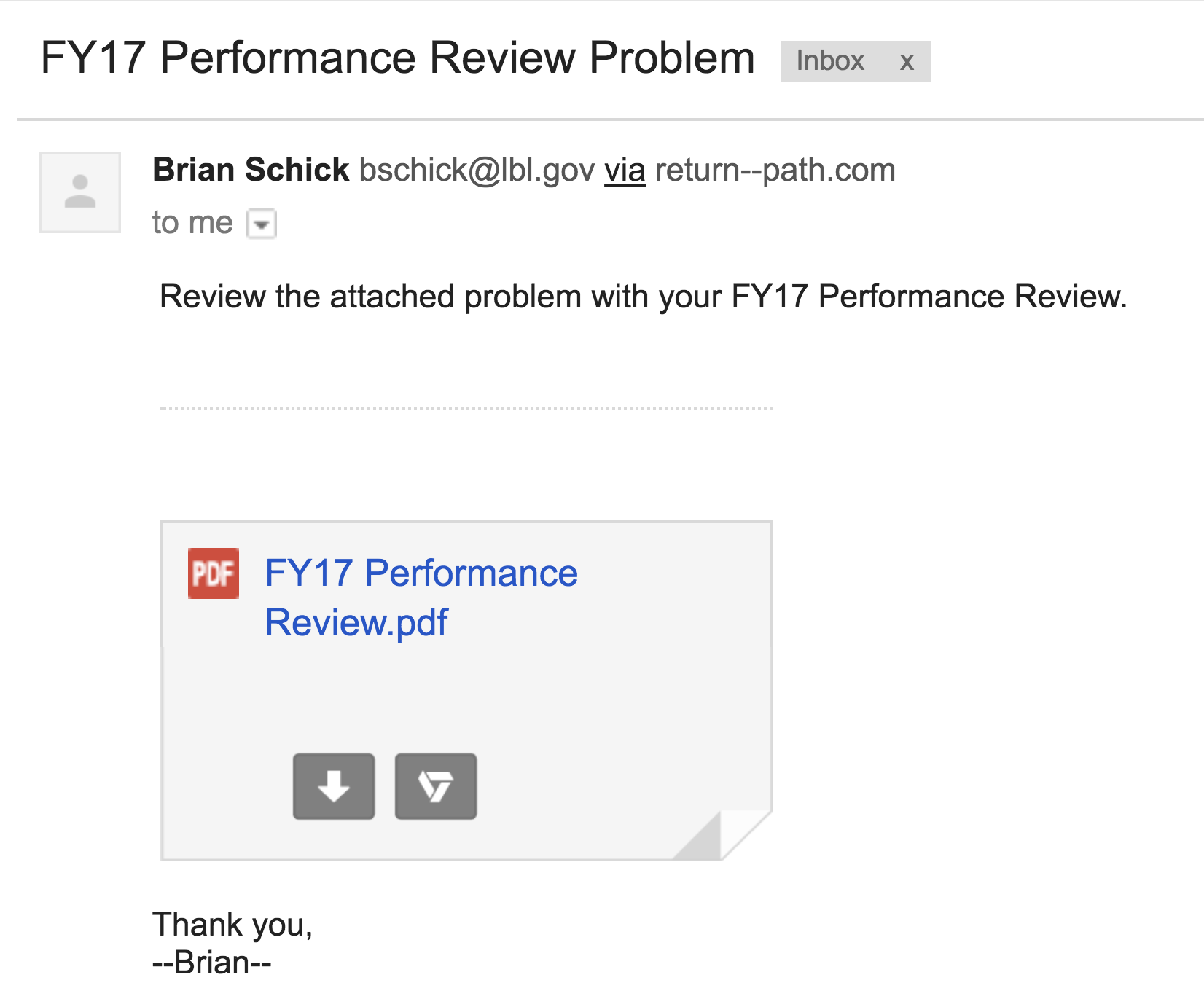
2017-10-16: FY17 Performance Review Problem
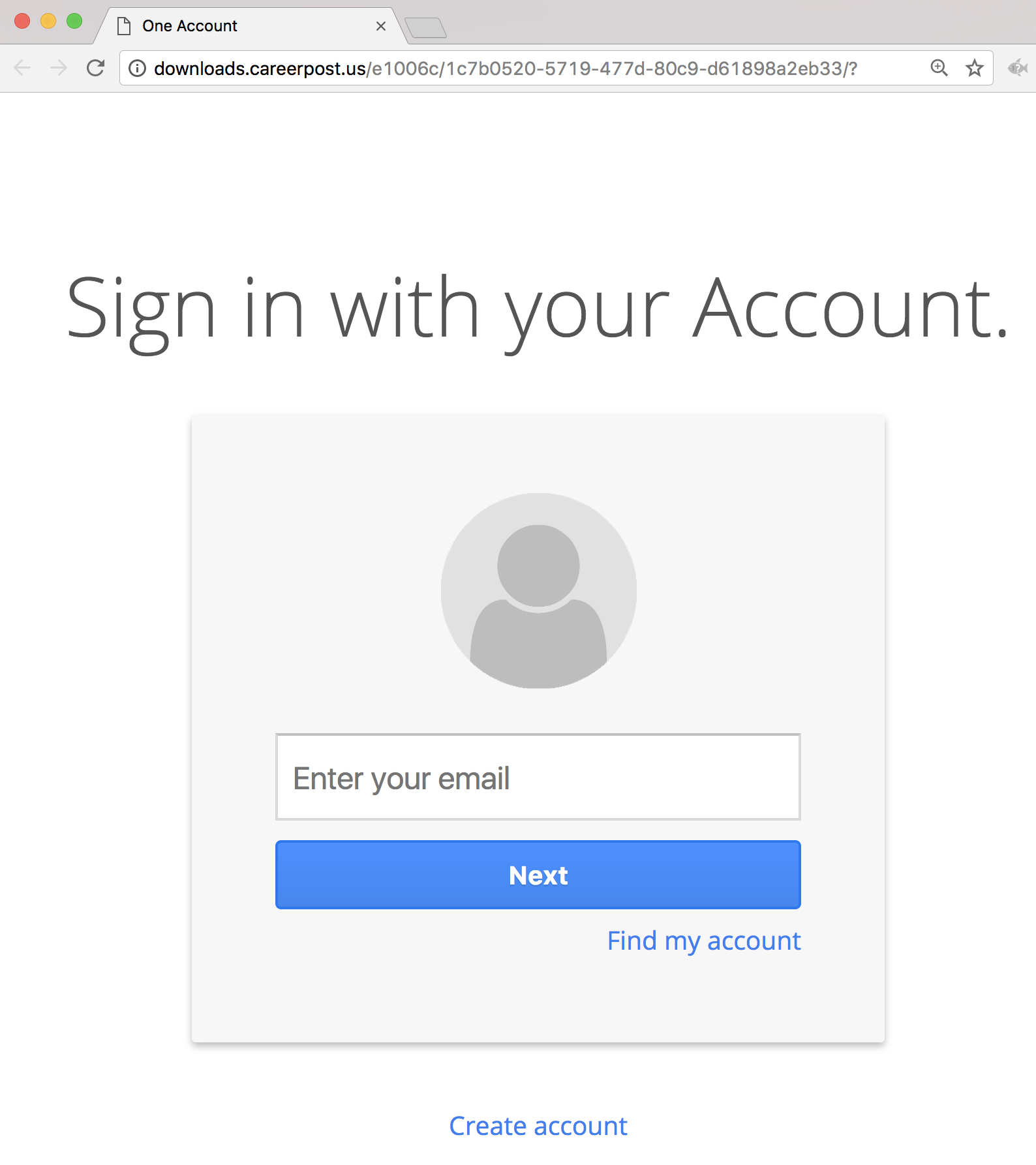
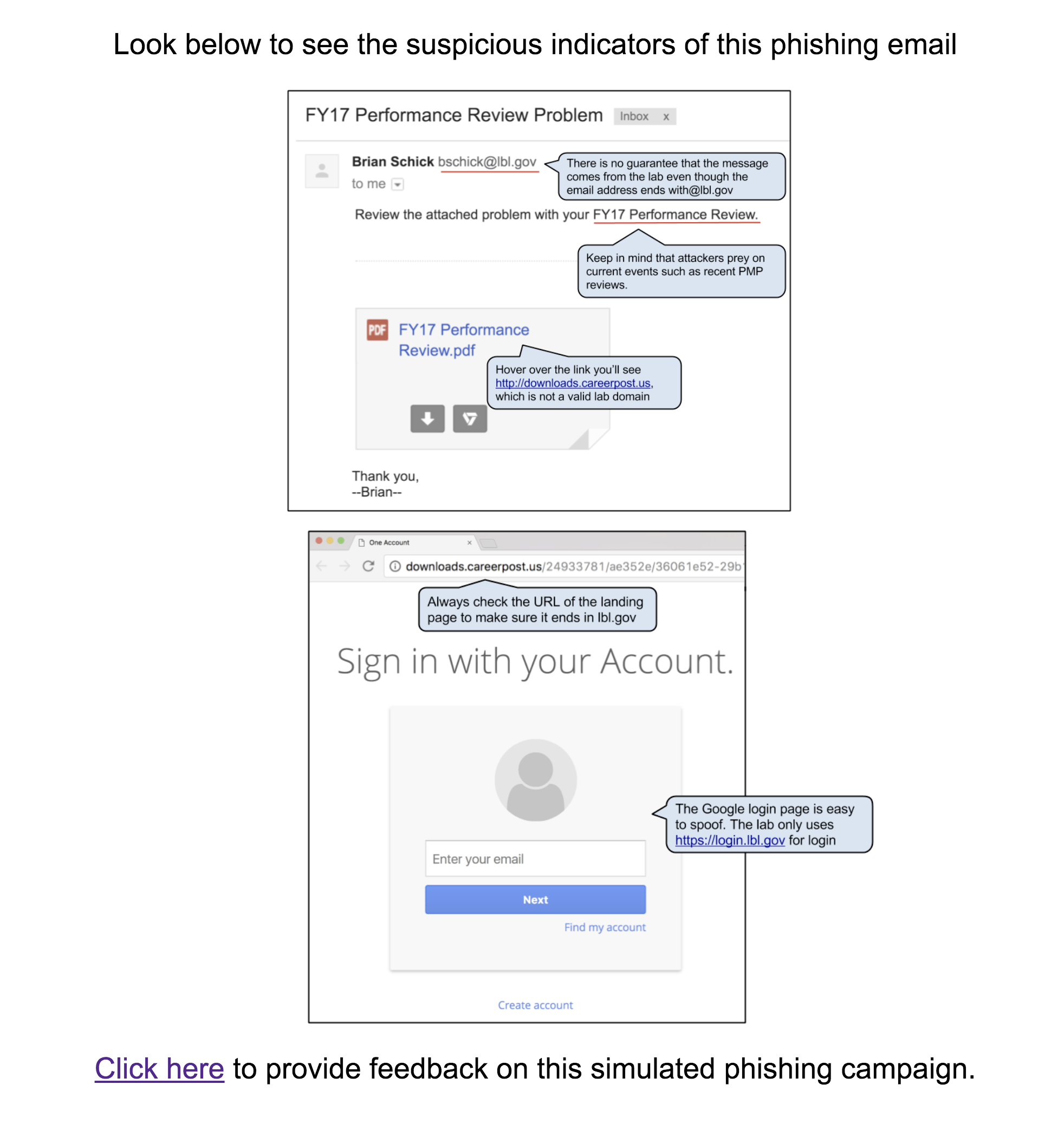
This email was intended to get users to question the legitimacy of the pdf attachment even though the sender appears to have a “real” lbl.gov email address. The attachment link in the email directed to a spoofed google login page in order to retrieve the username and password of the user. The fake employee Brian Schick was created to demonstrate the situation where an email address is spoofed or compromised. Emails sent to Brian was answered by the security group.
Users were expected check for Brian Schick on the directory as well as notice they were being asked to log in with LBL credentials to a non-LBL site.
Sender: Brian Schick - [email protected]
Link: http://downloads.careerpost.us/
The Email:
The Landing Page:
The Education Page:
2017-03-14: Employee evaluation
...