|
|
||||||||||||||||||
...
Below are screenshots of the simulated phishing campaigns that have been run so far at LBNL.
...
2017-
...
03-
...
14: Employee evaluation
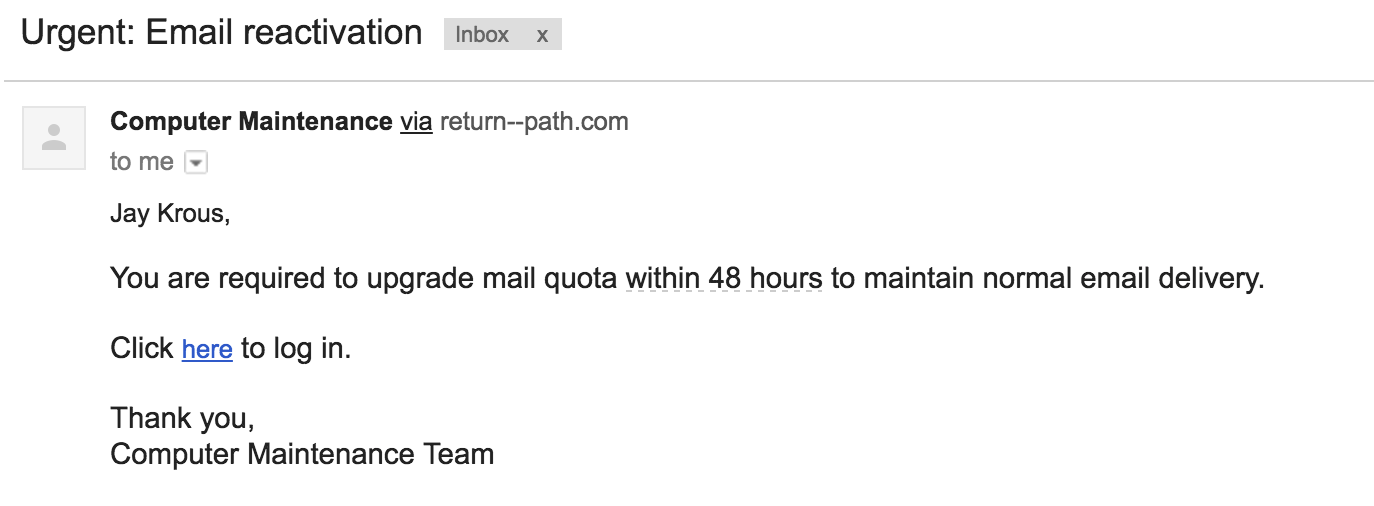
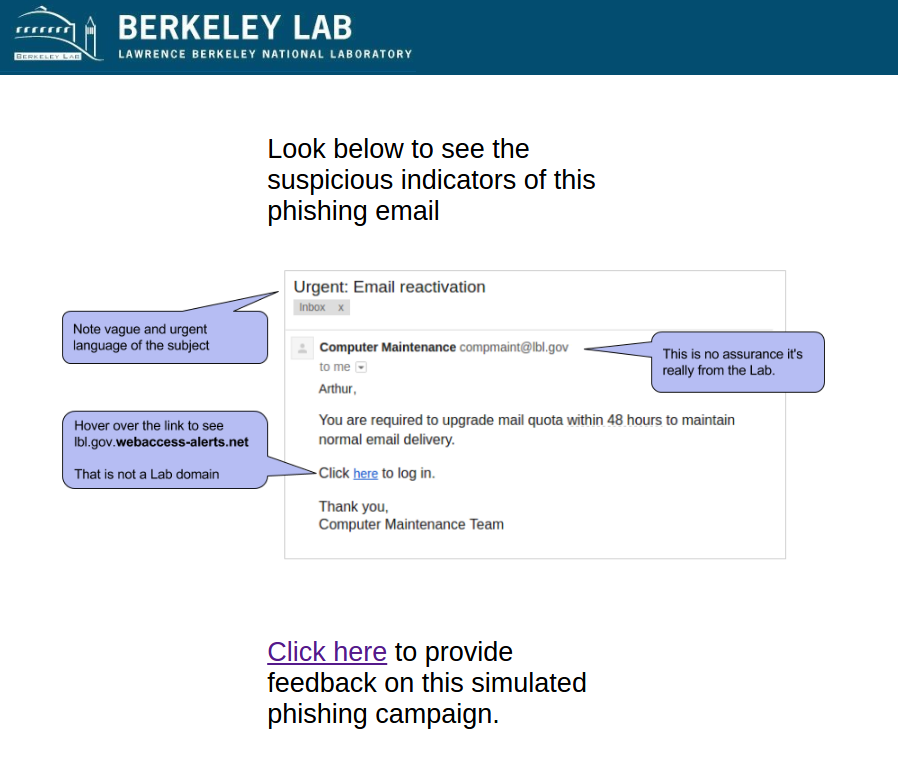
This email was our first phish and intended to test the waters. It emulated the common phishing emails that are vague, urgent, and not necessarily relevant. It had an fake sender address that appeared to be from within LBNL.
Sender: [email protected] - Computer Maintenance
Link: http://lbl.gov.webaccess-alerts.net/
The Email:
The Education Page:
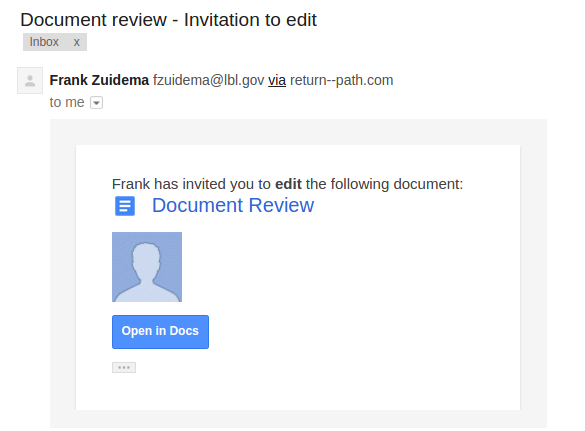
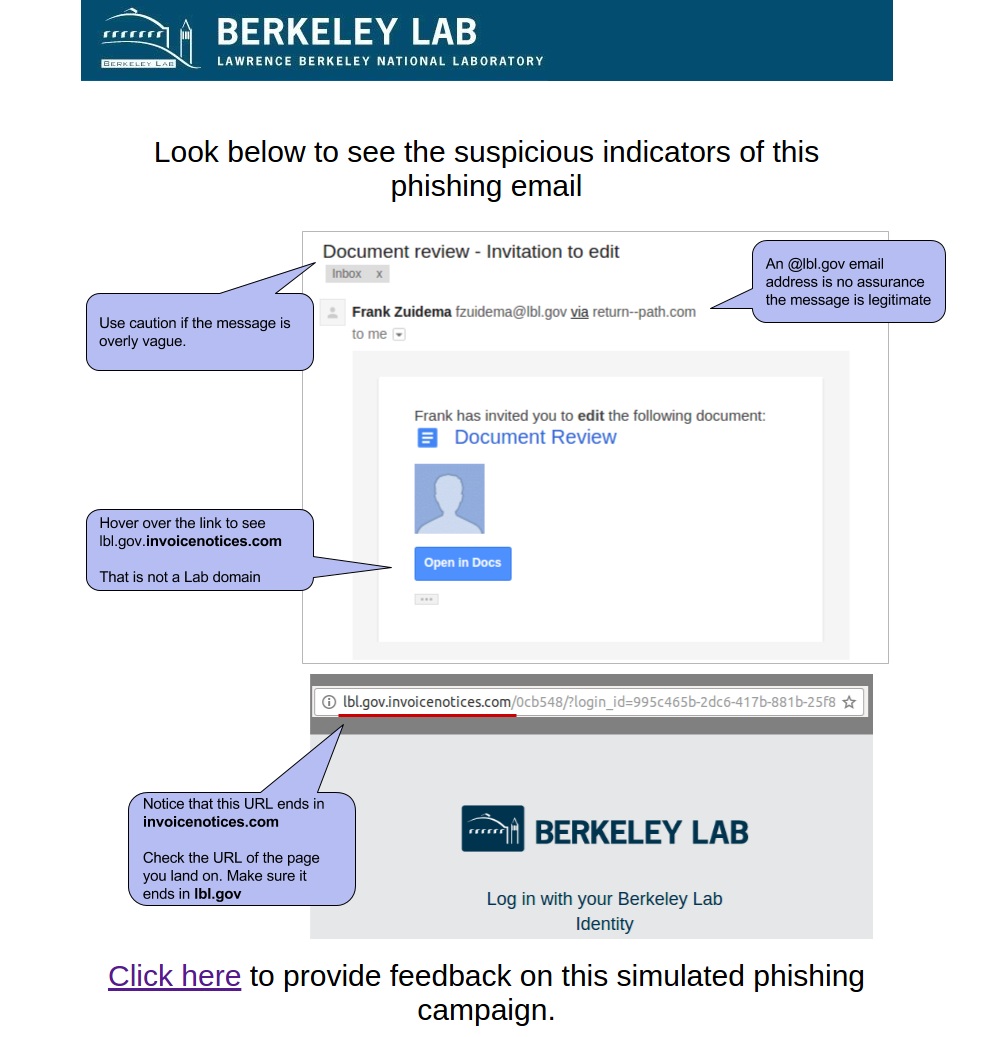
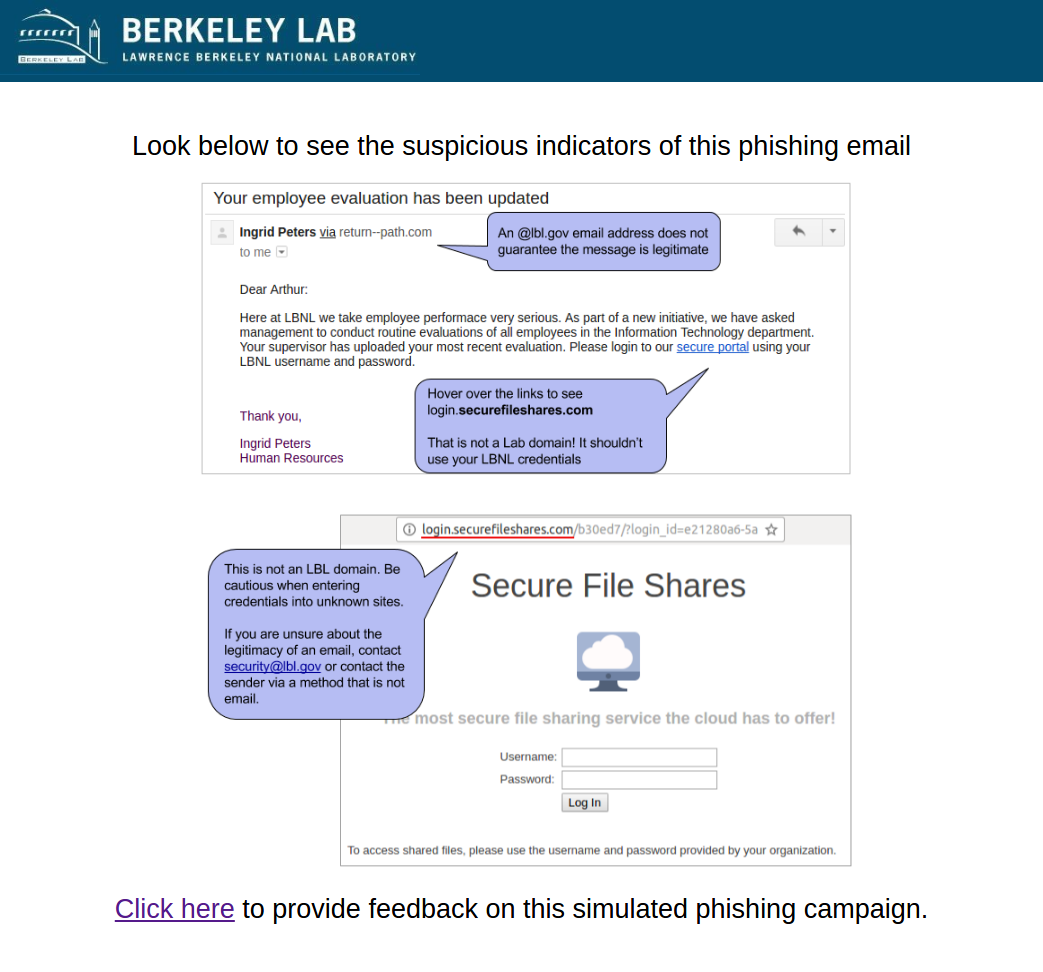
2016-12-06: Google Document Invitation to edit
This email was intended to get users to focus on the URL and demonstrate that it is often trivial to make a email or web site that looks like ones you trust. It mimicked the HTML of a real "Invitation to Edit" email sent by Google Drive as well as the LBL login page. The email appeared to be from an LBL employee (although this user doesn't exist)question the request to input credentials into a non-LBL site. The link in the email directed to a non-LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was reused from the previous phish. Ingrid was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security group.
Users were expected to notice the that they were being asked to log in with LBL credentials to a non-LBL link that the email directed to or check the existence of the sendersite as well as notice the reuse of the [email protected] address.
Sender: [email protected] - Frank ZuidemaIngrid Peters - [email protected]
Link: http http://lbllogin.govsecurefileshares.invoicenotices.com
The Email:
The Landing Page:
The Education Page:
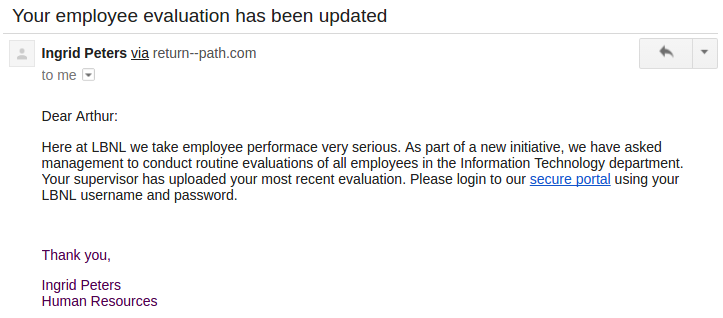
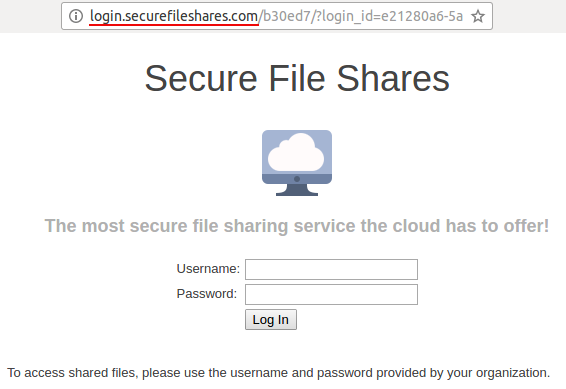
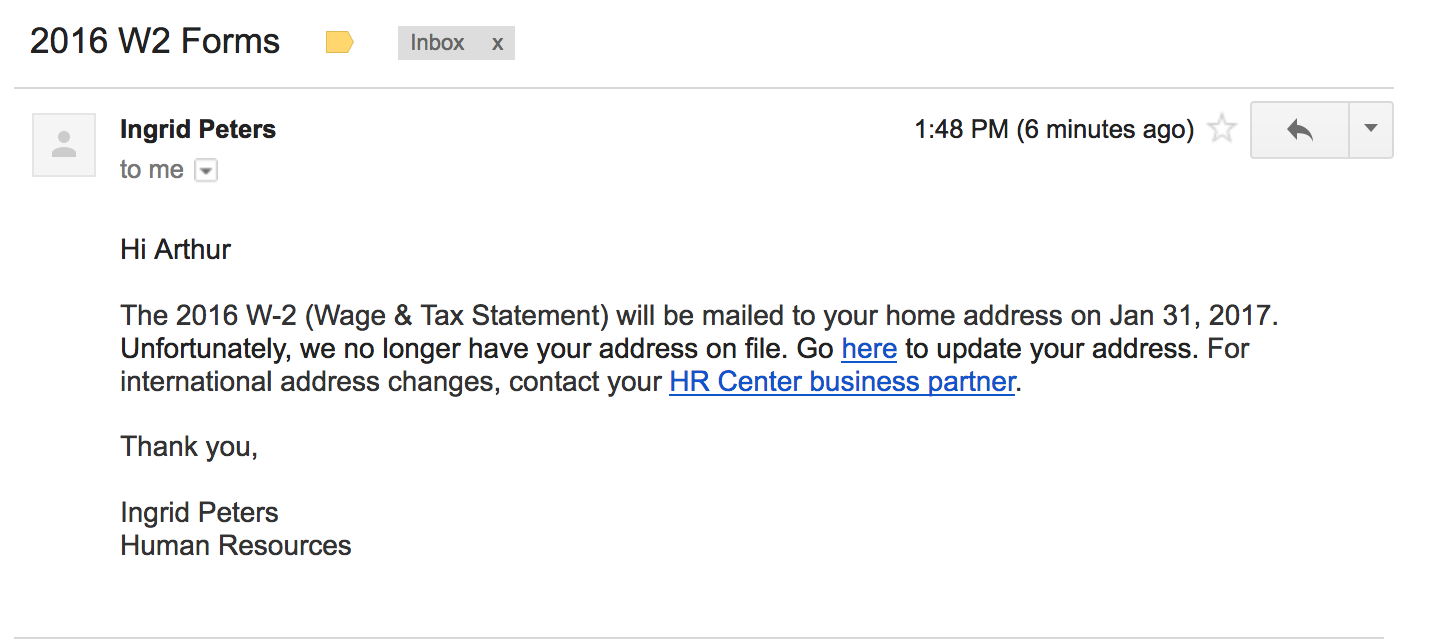
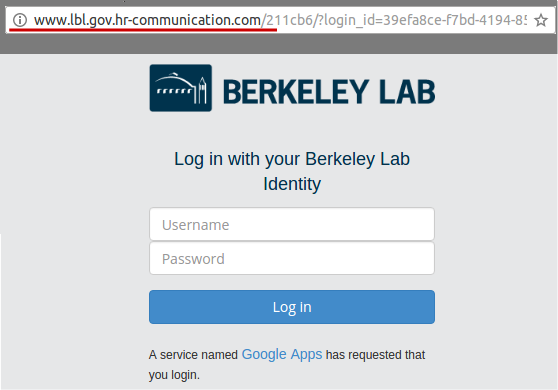
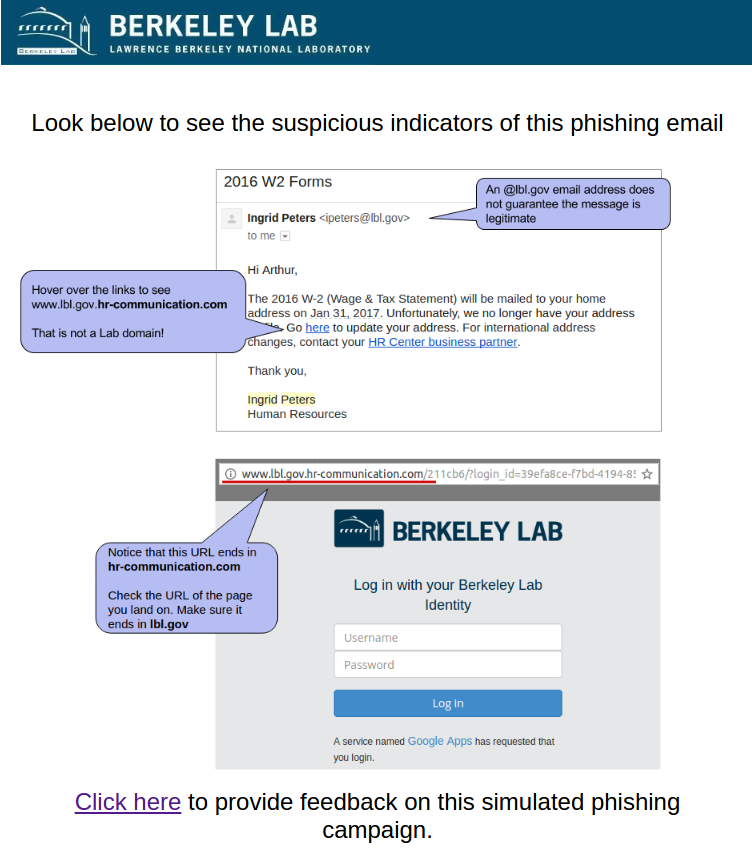
2017-01-18: 2016 W2 Forms - lost mailing address
This email was intended to get users to focus on the URL despite the use of a "real" lbl.gov email address. The link in the email directed to a fake LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security group.
Users were expected to notice the non-LBL link that the email directed to or to call the number for Ingrid Peters to check the validity of the email out-of-band.
Sender: Ingrid Peters - [email protected]
Link: http http://www.lbl.gov.hr-communication.com/
The Email:
The Landing Page:
The Education Page:
...
2016-
...
12-
...
06: Google Document Invitation to edit
This email was intended to get users to question the request to input credentials into a non-LBL site. The link in the email directed to a non-LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was reused from the previous phish. Ingrid was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security groupfocus on the URL and demonstrate that it is often trivial to make a email or web site that looks like ones you trust. It mimicked the HTML of a real "Invitation to Edit" email sent by Google Drive as well as the LBL login page. The email appeared to be from an LBL employee (although this user doesn't exist).
Users were expected to notice that they were being asked to log in with LBL credentials to a the non-LBL site as well as notice the reuse of the [email protected] address.
Sender: Ingrid Peters - [email protected]
link that the email directed to or check the existence of the sender.
Sender: [email protected] - Frank Zuidema
Link: http://lbl.gov.invoicenoticesLink: http://login.securefileshares.com
The Email:
The Landing Page:
The Education Page:
2016-10-08:
...
Urgent - Email Reactivation
This email was our first phish and intended to test the waters. It emulated the common phishing emails that are vague, urgent, and not necessarily relevant. It had an fake sender address that appeared to be from within LBNL.
Sender: [email protected] - Computer Maintenance
Link: http://lbl.gov.webaccess-alerts.net/
The Email:
The Education Page: