|
|
||||||||||||||||||
...
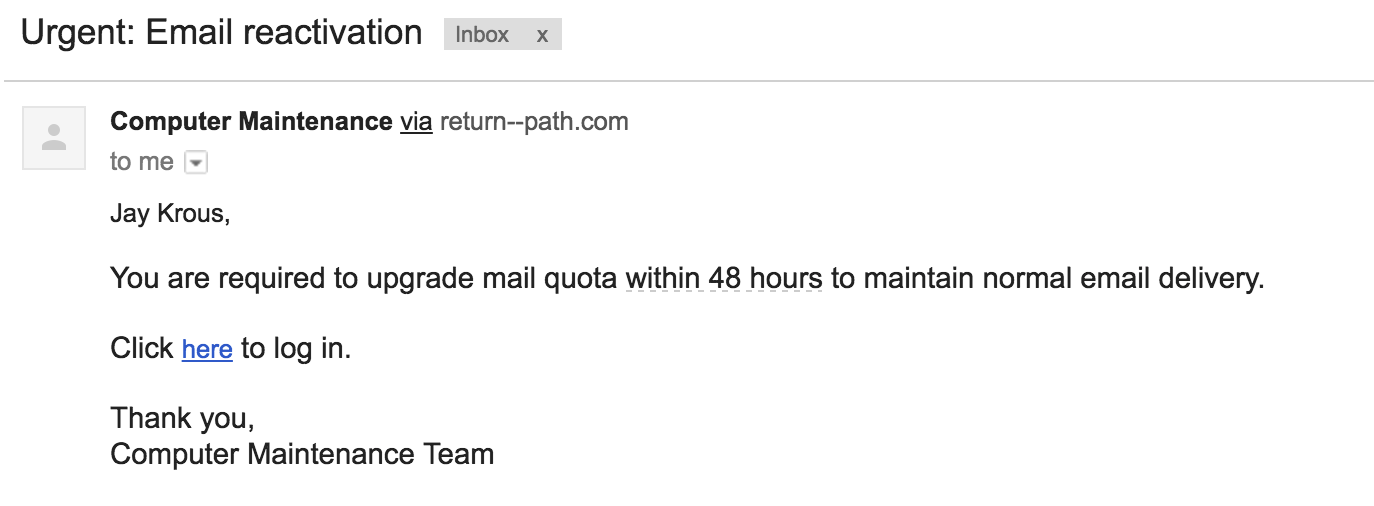
Sender: [email protected] - Computer Maintenance
Link: http http://lbl.gov.webaccess-alerts.net/
The Email:
The Education Page:
...
Users were expected to notice the non-LBL link that the email directed to or check the existence of the sender.
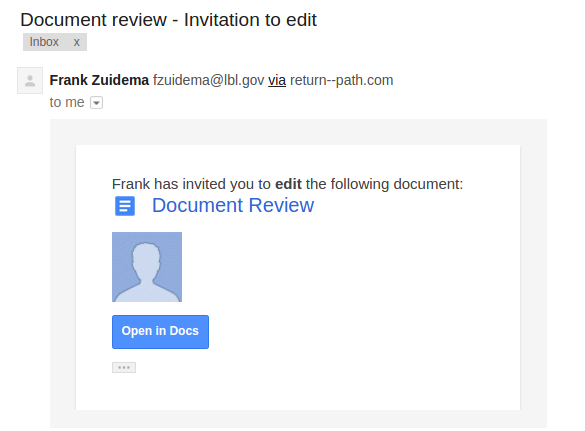
Sender: [email protected] - Frank Zuidema
Link: http://lbl.gov.invoicenotices.com
The Email:
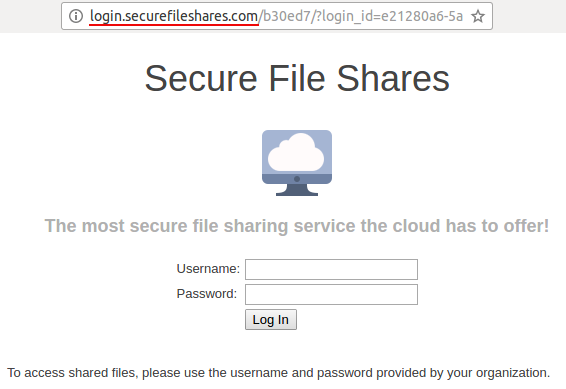
The Landing Page:
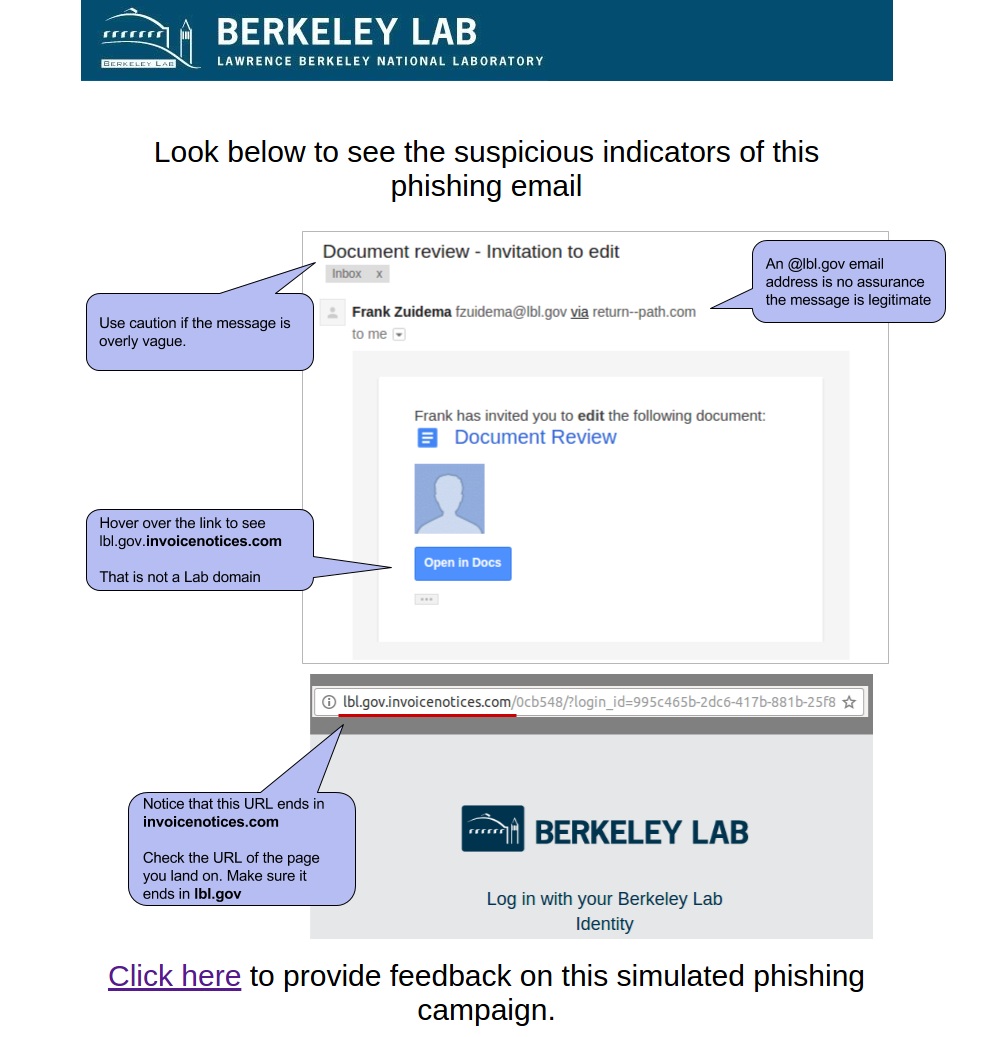
The Education Page:
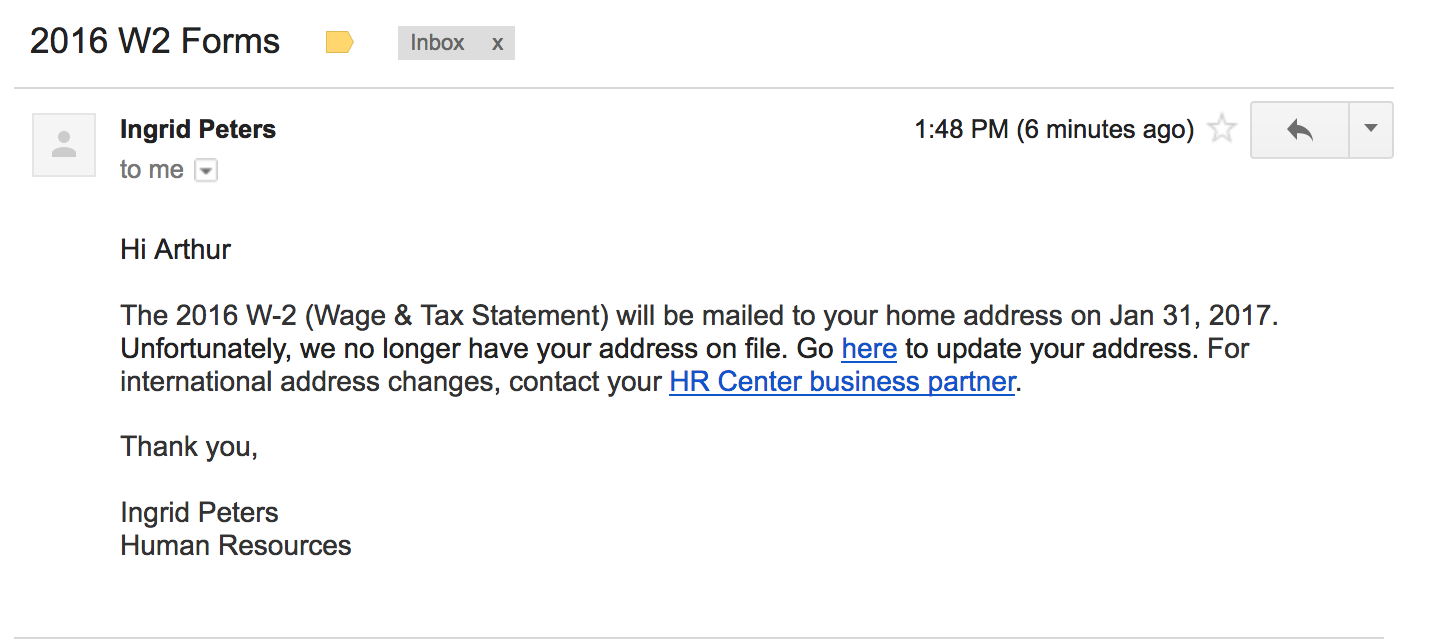
2017-01-18: 2016 W2 Forms - lost mailing address
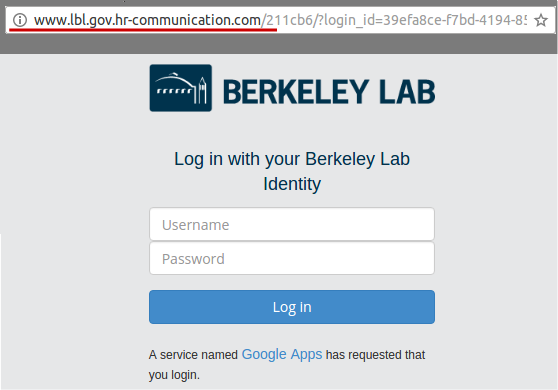
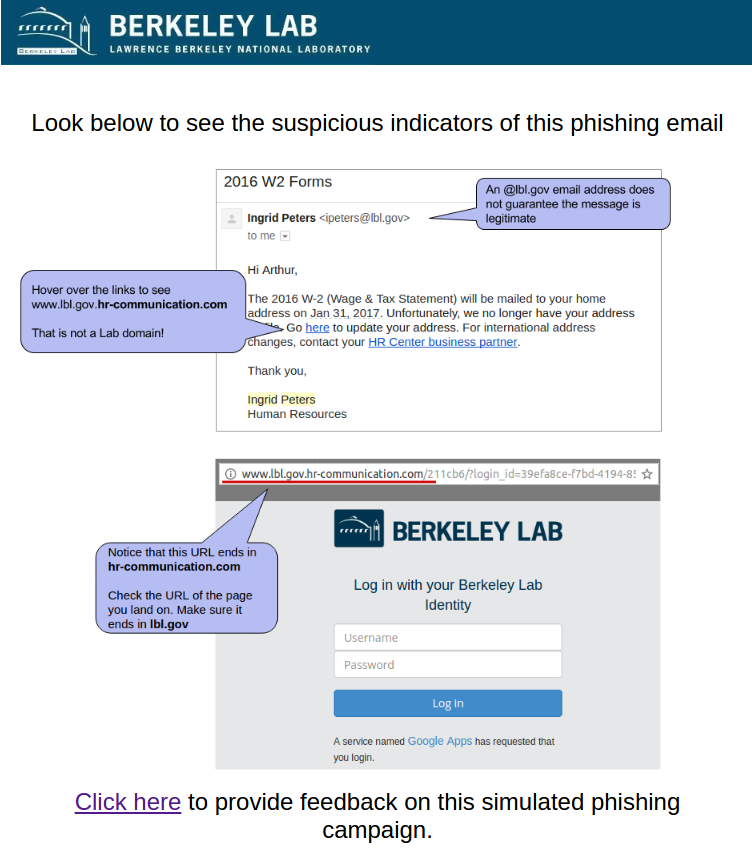
This email was intended to get users to focus on the URL despite the use of a "real" lbl.gov email address. The link in the email directed to a fake LBL login page in order to tempt users to enter passwords. The fake employee Ingrid Peters was added to the user directory to demonstrate the situation where an email address is spoofed or compromised. A phone number was added to Ingrid's directory entry that would be answered by security group.
Users were expected to notice the non-LBL link that the email directed to or to call the number for Ingrid Peters to check the validity of the email out-of-band.
Sender: Ingrid Peters - [email protected]
Link: http://www.lbl.gov.hr-communication.com/
The Email:
The Landing Page:
The Education Page: