Berkeley Lab is serious about protecting your personal information. While most of our work is open and publishable, certain types of operational and research information must be protected according to Federal and State Law, as well as our own good judgment. For more information about the Program, please review the below sections (click to expand/collapse text).
Laboratory Privacy Officer and Program Governance
The Laboratory has an appointed Privacy Officer and to oversee the implementation of LBNL's Privacy Program. The Privacy Officer heads a Privacy Steering Committee composed of members across the Laboratory tasked with the primary functions of managing privacy risks, such as ensuring newly emerging issues are addressed proactively and collaboratively.
If you have any questions about the Program or protecting personal information, contact the privacy officer at privacy@lbl.gov.
Program Vision
As declared in the University of California Statement of Privacy Values, privacy is fundamental for the success of a research institution. In this context, privacy is understood as “(1) an individual’s ability to conduct activities without concern of or actual observation, and (2) the appropriate protection, use, and release of information about individuals.” To implement controls consistent with this understanding, LBNL must adequately balance (1) fostering and preserving individual end user privacy with (2) handling personal information pursuant to legal, regulatory, and contractual requirements. This policy and related implementation documents guide the Laboratory in striking that balance by accomplishing the following:
ensuring an appropriate level of privacy protection across business processes, even as interpretations of privacy change over time;
nurturing an environment of openness and creativity for research;
honoring its obligation as a public institution to remain transparent, accountable, and
operationally effective and efficient; andsafeguarding information about individuals and assets for which it is a steward.
Statement of Values
Consistent with UC Policy and Fair Information Practices Principles (FIPPs), LBNL’s privacy program core values are autonomy and information privacy as discussed below.
Autonomy Privacy:
LBNL’s privacy program is driven by the need to create an environment where individual members of the laboratory community can exercise a substantial degree of control over their expressions, associations, and general conduct without unreasonable oversight. Guided by First Amendment principles, LBNL is committed to encouraging its members to exercise free inquiry and discourse without fear of reprisal or intimidation, subject to the privacy and safety of other individuals or Laboratory resources. Moreover, the Laboratory is committed to respecting the privacy of individuals, including their interactions with others, and expects Laboratory members to esteem each other’s privacy and well-being. Lastly, the Laboratory is guided by state and federal constitutional principles regarding surveillance of persons or places, whether in person, on campus, or electronically, and is committed to balancing the need for security of individuals and laboratory property with the individuals’ reasonable expectations of privacy.
Information Privacy:
LBNL’s privacy program is also driven by the need to ensure that information is adequately protected to reduce privacy risks to acceptable levels and to give data subjects a true understanding of how their data is processed by the laboratory. Under this rubric, the laboratory is guided by the additional principles:
Data Minimization. LBL will only collect Personal information that is relevant and minimally necessary to accomplish stated business purposes. In the absence of an ongoing business need to process the information, LBNL shall refrain from collecting and appropriately dispose of such information in accordance with applicable records retention policies.
Transparency: LBNL will provide clear and advance notice of its information policies and practices for collecting, using, disclosing, retaining, and disposing of (“processing”) information about individuals.
Choice: LBNL will provide individuals with reasonable opportunities to choose whether to and by what means to provide their information prior to collecting, using, disclosing, or retaining their information. However, when the information about the individual is necessary to deliver a service or benefit or to participate in an activity, the individual may be required to provide the information in order to receive the service or benefit, or to participate.
Information Review and Correction: LBNL will provide individuals with a way to review the information about themselves that they have provided or permitted to be collected, as well as a procedure to request the correction of inaccuracies and one to perform the correction if appropriate.
Information Protection: LBNL will adequately secure the information about individuals under its stewardship by providing appropriate employee training and by implementing administrative, technical, and physical controls aimed at properly protecting personal information against breach.
Accountability: LBNL employees will be aware of and be held accountable for furthering the goals of this policy and remaining in compliance with relevant procedures or requirements. When appropriate, LBNL will take action by investigating reported violations of information privacy principles and policies and, as appropriate, taking corrective measures.
Personal Information
Personal information consists of any information processed by LBNL staff in support of official laboratory business which relates to or describes an identifiable individual. Personal information is an overarching term that encompasses highly sensitive personally identifiable information (personal information subject to legal, regulatory, or contractual obligations), prudent to protect personal information, and publicly available information (such as directory information or information that is lawfully made publicly available by government agencies).
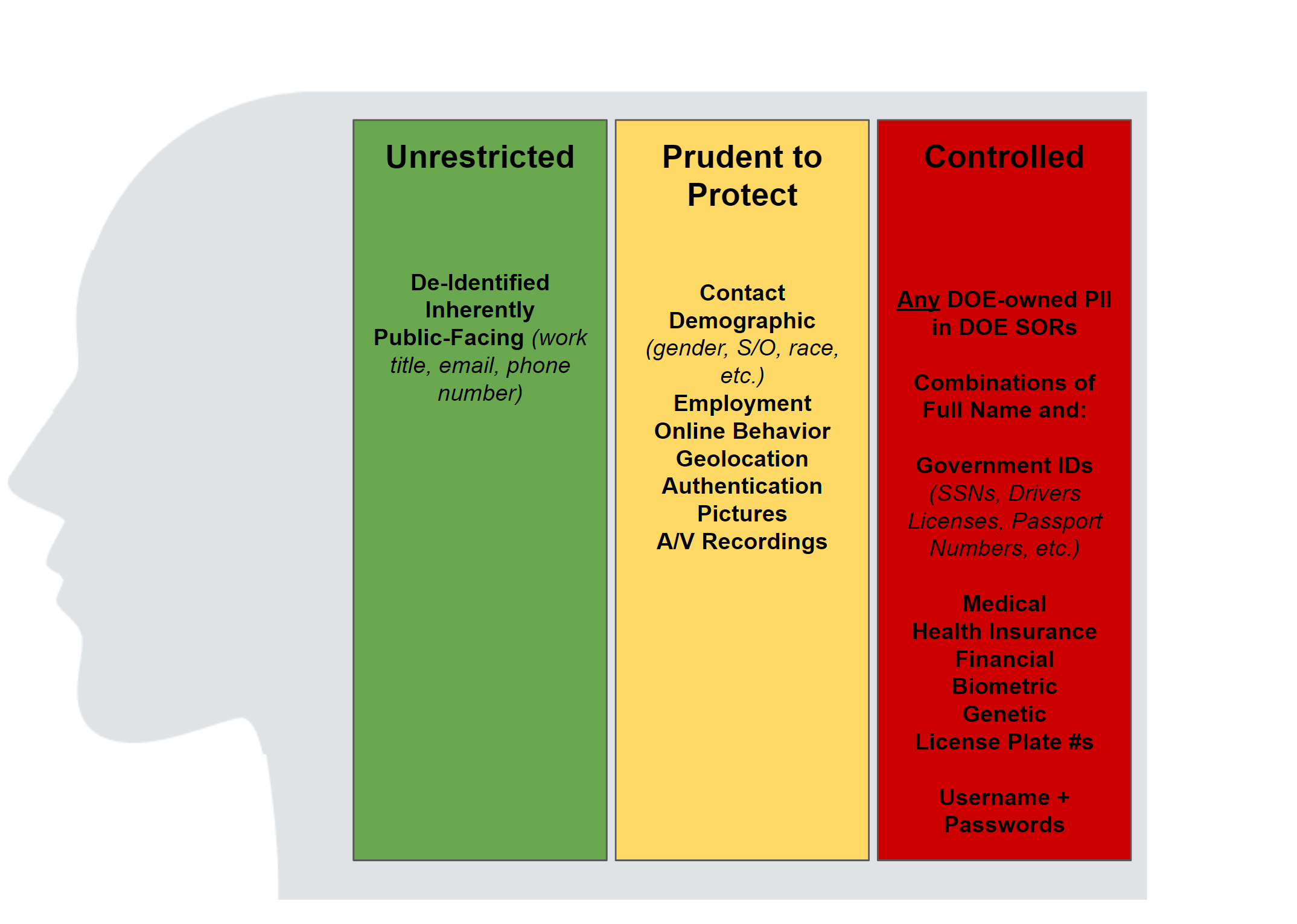
The below figure provides a high-level overview of the different kinds of personal information and their inherent risk profile.
Personal Information Rated "Protected" - High Risk Personal Information
Data elements under the PII category are the most sensitive types of personal information at the Lab. Any use, transmission, storage, destruction, or other processing of PII must be approved by the IT Division. Any actual
Data Breach-Notice triggering Personal Information (under the California Information Practices Act, Cal. Civ. Code 1798.29), specifically:
Government Identifiers: Social Security Numbers, Drivers License Numbers, Passport Numbers, Green Card Numbers, and any other government-issued identifiers commonly used to identify an individual
Employee health information, including records originating from a healthcare provider containing descriptions of conditions, diagnosis, prescriptions, referrals, visits, and other health information, insurance and/or claims-related information.
Biometric Information
License Plate Recognition System information
Financial account information (such as debit and credit account information), including PINs or other authentication information
A combination of first name or first initial and last name and:
Usernames and Passwords that would permit someone to access an online account.
Personally Identifiable Information stored in Department of Energy-owned records maintained in Privacy Act Systems of Records
Certain Sensitive Personal Data of EU residents contained in records subject to the General Data Protection Regulation.
Certain datasets determined to be highly sensitive pursuant to a documented risk assessment by the Privacy Officer.
Personal Information Rated "Prudent To Protect"
The below data categories and elements are included in the definition of personal information and are generally regarded as "Prudent to Protect." Note that certain information collections containing purely prudent-to-protect information may be regarded as highly sensitive depending on a number of factors, including the total number of data elements for any one individual, the number of individuals and records present in the data set, and other factors.
- Contact Information: home address, home telephone number.
- Demographic Information: Gender, Gender Identity and Expression, Sexual Orientation, Racial or Ethnic Origin, Religious Affiliation, Political Beliefs, Date of Birth, Disability Status, Veteran Status, Salary.
- Employment-Related Information: employee performance information, credit reports, drug test results, information related to the processing of security clearances, certain kinds of employee health records, job-application information, education information.
- Online Behavior: web browsing history, IP Address, MAC Address, Email Address, Usernames, social media-related activities performed through an individual’s personal account.
- Precise Geolocation
- Authentication Information: answers to security questions (mother’s maiden name, favorite childhood friend, etc.).
- Pictures, audio, and/or video recording: CCTV Captures, Meeting Recordings
Personal Information not rated Prudent to Protect or Controlled
The below data categories and elements are included in the definition of personal information but are not subject to controls beyond what applies to information generated in the course of pursuit of LBNL's mission (such as information intended for publication).
- Directory Information: this consists of information related to an individual published to facilitate contact with LBLN workforce members. This consists of information made publicly available on phonebook.lbl.gov such a your name, work email, phone, mailbox, and office information.
- De-Identified Information: this consists of personal information previously considered prudent to protect or controlled, but which has been rendered unidentifiable through one of many processes, such as pseudonymization and anonymization.
Privacy Training
- SEC0201 - Cyber Security Annual Training (SEC 0201) - required of all workforce using computers.
- SEC0203 - Notice of External Monitoring SEC 0203
- SEC0220 - Protected Information Training
Privacy Notices
Privacy Forms
Privacy Data Subject Requests (access, correction, erasure, disclosure)
1 Comment
Felecia Harris
work hard